Lock Your Digital Windows and Doors: Basics of Digital Security
- July 22, 2017
- by Emily

When I lived in Russian in 2003 and 2004, my email account was hacked on a semi-regular basis and used to send spam to others. My account would get blocked, and I would have to call my mom and have her reset the password on my AOL account.
It was annoying, but had limited financial ramifications other than the cost of a call home.
If my - or your - email account were to be compromised today, it would have more serious consequences. In 2004, I didn’t use online banking or have a PayPal account. Now I do, and both of those things could be accessed if my email were hacked.
Hacking email is far from the only way that malicious users could mess up your digital life. Here are a few basics for keeping yourself and your data secure from hackers and identity thieves.
Run Software Updates Frequently
Software companies are constantly finding new vulnerabilities in their products. Those little problems are part of the reason they release upgrades. The more time a particular software version has been around, the more time hackers have had to figure out how to exploit those vulnerabilities.
So updating your browser, apps, and your operating system is not just a way to get things to open a couple milliseconds faster. It is actually one of the easiest, most basic ways that you can increase your digital security.
You should aim to update all of your software, including browsers and operating systems, as soon as possible after new versions become available. Most of the time programs will prompt you to install updates. They are annoying but come with some digital peace of mind.
Get a Password Manager
If your password is KIDONEkidtwo12345, and you use the same password for absolutely everything, from your online banking to your Apple account to the Mealtrain account you set up when your first child was born, you need some variety in your life.
Passwords present a paradoxical challenge, because you are supposed to create these difficult, random streams of characters but then use them every time you need to log in to Instagram. The problem with using just one password for everything is, once a hacker guesses it correctly (or discovers it through a leak) they can use it to get into everything else, including your financial information, all without even having to trigger a password reset which you may notice. The system is not designed for compliance or ease of use for humans. Which is why password managers are so great.
Password managers create and store long, random passwords. You just have to remember the master password for your password manager, and you’ll be able to access everything else easily with a higher degree of security. Password managers work by unlocking your list of passwords with a master password. From there you can copy and paste the random password into the password prompt for the account you are trying to sign into. You can also use a password manager to keep the account URL, username, what email you used, the last time you changed the password, notes, etc. They can be especially helpful at generating new strong passwords that match the rules for the site.
To take the idea of using random passwords a step further you may also consider using fake answers to the pesky security questions some sites want, and store those in the notes field of your password manager for the associated account. That way even if someone knows you were born in Springfield, and your first pet was named Santa’s Little Helper, it wouldn’t be useful for hacking your account.
Some options for password managers include KeePass (free and open source), 1password ($36/year), Dashlane ($40/year) and Padlock (free and opensource).
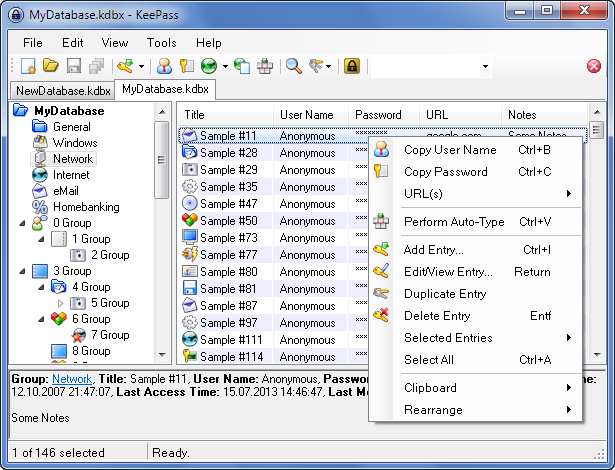
After you get your password manager setup make sure you backup the file on a regular basis! This step is not applicable with cloud based password managers, but it is with tools like KeePass which use a local file to hold you passwords). If you lose all your passwords, you are faced with triggering password resets to your email or calling up the associated companies to get access established. Carrying a USB stick on your keychain with a backup of the file is one way to always keep it with you.
KeePass has an extra security option designed to block access to your passwords even if your password safe file falls into the wrong hands. It allows you to configure how many transformations the password goes through before it is used to try and unlock the file. A higher value means each attempt causes the CPU to cycle for a given amount of time. When that option is set to a high value it prevents hackers from being able to systematically guess your password, since it would take them eons to walk through all the possible combinations. For more on that see: "A KeePass setting that might save your online identity".
Rotate Your Passwords
Changing your password often is a good idea. Smart hackers are known to watch your email / account data for months before moving against you. If a hacker can see your email they can learn a lot about your finances and your life, like when you will be on vacation. Changing your password often limits that possibility.
Keep work, finance, and personal email accounts separate
The achilles heel of online account security is the account’s email address. If that is compromised, a hacker can use it to trigger a password reset or ‘forgot password’ request. When that is complete, they can not only get into the account and impersonate you, they can lock you out of it by updating the email on the account to their own.
One strategy to prevent that is to use different email accounts for different purposes. For example, you might have one account for personal stuff and social media. That account is used to keep in touch with friends and family, online shopping, signing up for newsletters and other spammy stuff. A second, totally independent email could be used exclusively for online banking, brokerages and credit cards. Nobody else would know about your ‘financial’ email account. It could be something random like bingo123red@gmail.com which doesn’t even personally identify you.
This solution is not foolproof but does create silos between the sensitive accounts and the more exposed, personal accounts.
Use Two-Factor Authentication Where Possible
For your most sensitive log-ins, you should set up two-factor authentication. You would want this on anything financial, but also on your primary email account. Again, don’t underestimate how much damage can be done with just access to your email.
Two-factor authentication means that anyone who tries to log in to one of your accounts will have a temporary password sent to his or her phone, either through SMS text or through a messaging app. Just having the password - the first factor “what you know” will not be enough to access the account. To get in you also need the second factor “what you have”, typically your smart phone.
Some services allow the use of app, rather than text messages, for two-factor authentication, but it varies by service. For example AWS supports Authy and Google Authenticator on a smartphone, or you can purchase a hardware device just for this purpose.
Encrypt Your Hardware
Even if you’ve done everything, you might still be vulnerable if your laptop or phone were stolen. So it’s a good idea to make sure that simply having your device isn’t enough to access your sensitive information.
If you have a newer iPhone that requires a passcode to unlock, your phone is probably already encrypted. That means not only do you need a passcode to access the phone, but the actual files are encrypted.
If you have an android phone, you’ll need need to encrypt your phone yourself. Here’s an article from Google outlining how to do so.
Although your phone is more likely to be stolen than your laptop, it’s also a good idea to encrypt your laptop. If you have a Mac, you can use FileVault to encrypt your laptop or desktop (included with Mac OS). If you have a Windows machine, you can use BitLocker (included with some versions of Windows) or VeraCrypt (free / open source) to secure your files. On Linux, Ubuntu comes with built in disk encryption.

The bottom line is that if you take these steps to increase your digital security, you’ll be more secure than most people. That is enough to dramatically reduce the likelihood of being hacked. Just like a burglar will look for the most vulnerable house in the neighborhood, a hacker will attack the most vulnerable digital accounts. If you’re more protected than your neighbors, digitally speaking, you are less likely to be a hacking victim.








